Security of SCADA Systems
In today’s interconnected world, where technology permeates nearly every aspect of our lives, the security of supervisory control and data acquisition (SCADA) systems has become paramount. These systems, utilized in various industrial sectors, play a pivotal role in monitoring and controlling critical infrastructure, including electricity grids, water treatment plants, oil refineries, and transportation networks. However, the increasing connectivity and reliance on digital technologies have also exposed SCADA systems to a myriad of cybersecurity threats, ranging from malicious hackers to insider errors. In this comprehensive guide, we will delve into the intricacies of SCADA security, exploring its importance, vulnerabilities, and best practices to fortify these critical systems.

What Is a SCADA System?
SCADA systems, an acronym for Supervisory Control and Data Acquisition, are sophisticated networks designed to monitor and control industrial processes in real-time. These systems consist of hardware components, such as sensors, actuators, and programmable logic controllers (PLCs), interconnected through a network infrastructure. Additionally, SCADA systems incorporate software applications for data acquisition, visualization, and control, enabling operators to remotely monitor and manage industrial operations efficiently. The seamless integration of hardware and software components allows SCADA systems to gather data from various sensors, analyze it, and provide actionable insights for optimizing industrial processes.
Learn more about how SCADA Systems are utilized for Agricultural Irrigation here.
SCADA Architecture and Components
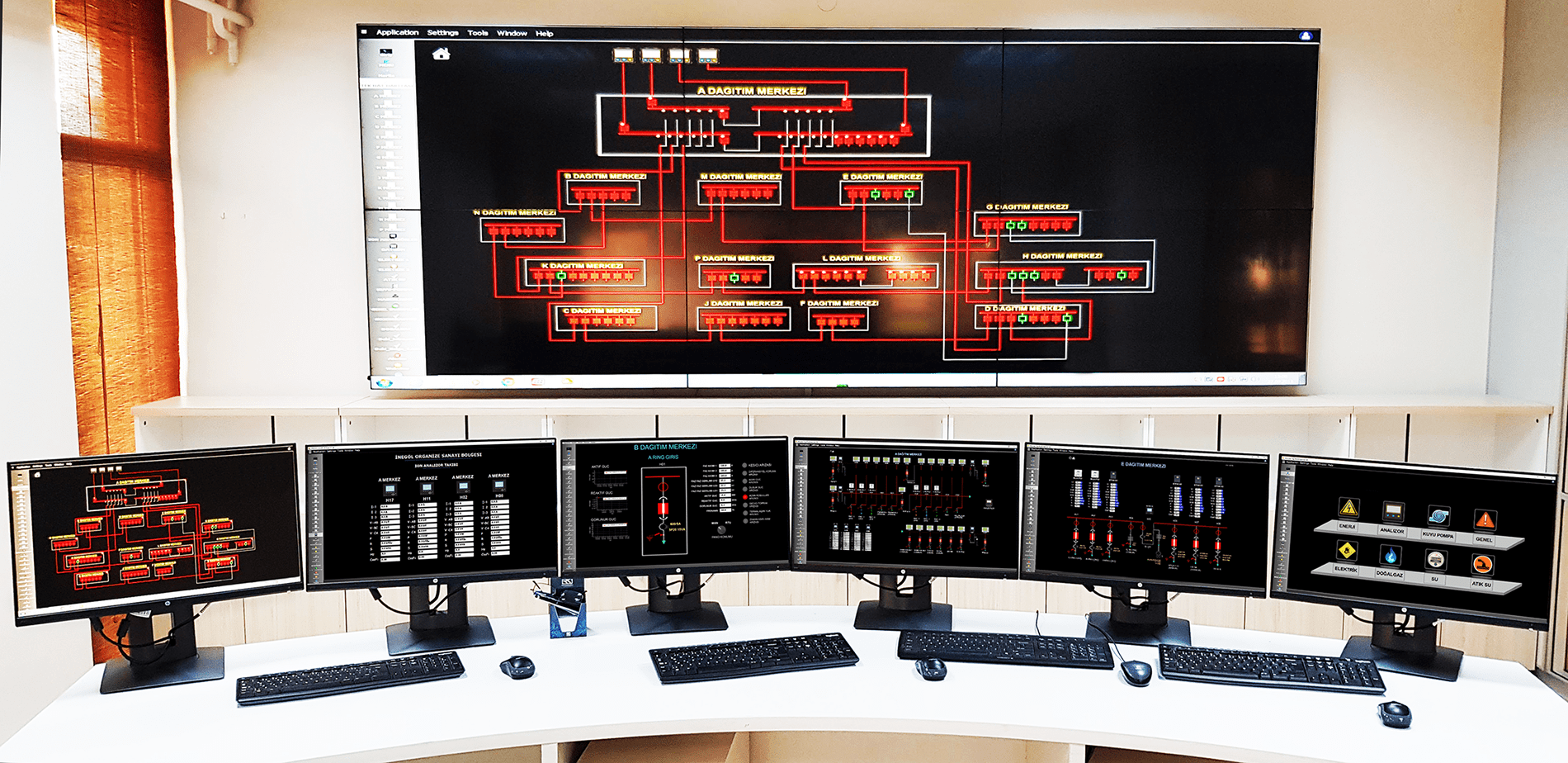
A typical SCADA system comprises several interconnected components, each serving a specific function within the network architecture. These components include the Human-Machine Interface (HMI), which serves as the primary interface for operators to interact with the SCADA system, providing graphical representations of industrial processes, real-time data visualization, and controls for monitoring and managing operations. Additionally, Remote Terminal Units (RTUs) and Programmable Logic Controllers (PLCs) act as hardware devices responsible for interfacing with sensors, actuators, and other industrial equipment. They collect data from sensors, execute control commands, and communicate with the supervisory control center. The communication infrastructure plays a crucial role in facilitating data transmission between various components of the SCADA system, including field devices, RTUs, PLCs, and the supervisory control center. It may comprise wired or wireless networks, such as Ethernet, serial communication protocols, or radio frequency (RF) communication. Lastly, the supervisory control center serves as the central hub for monitoring and controlling industrial processes, aggregating data from field devices, analyzing it, and providing operators with real-time insights to make informed decisions.
SCADA Vulnerabilities and Threats
Despite their critical importance in industrial operations, SCADA systems are vulnerable to a wide range of cybersecurity threats and vulnerabilities. These threats can potentially compromise the integrity, availability, and confidentiality of industrial processes, leading to operational disruptions, financial losses, and even safety hazards. Some common vulnerabilities and threats to SCADA systems include:
Cyberattacks: Malicious hackers often target SCADA systems with cyberattacks aimed at gaining unauthorized access, disrupting operations, or causing physical damage to industrial infrastructure. These attacks may exploit vulnerabilities in network protocols, software applications, or human factors to compromise the security of SCADA systems.
Malware: Malicious software, such as viruses, worms, and ransomware, pose a significant threat to SCADA systems. Malware infections can disrupt operations, steal sensitive data, or render industrial equipment inoperable, leading to production downtime and financial losses.
Insider Threats: Insider threats, including disgruntled employees, contractors, or third-party vendors, pose a significant risk to SCADA security. Insider threats may involve deliberate sabotage, negligence, or inadvertent errors that compromise the confidentiality, integrity, or availability of industrial processes.
Physical Security Risks: Physical security risks, such as unauthorized access, tampering, or sabotage of industrial equipment, can have serious consequences for SCADA systems. Physical attacks on critical infrastructure, such as power substations or water treatment plants, can disrupt operations and pose safety hazards to personnel and the environment.
Explore the implementation of SCADA Systems in the Mugla City Water and Sewerage Administration (MUSKI) Water SCADA System here.
SCADA Security Best Practices
To mitigate the risks posed by potential threats and vulnerabilities, organizations must adopt a proactive approach towards SCADA security. Implementing robust security measures and best practices can help safeguard SCADA systems against cyberattacks and ensure the integrity and availability of industrial operations. Some key best practices for SCADA security include:
- Network Segmentation: Segmenting the SCADA network into isolated zones or subnetworks can help minimize the impact of cyberattacks and prevent unauthorized access to critical infrastructure. Implementing firewalls, access controls, and intrusion detection systems can help enforce network segmentation and enhance the security of SCADA systems.
- Strong Authentication and Access Controls: Implementing strong authentication mechanisms, such as multi-factor authentication (MFA) and role-based access controls (RBAC), can help prevent unauthorized access to SCADA systems. Limiting access privileges based on job roles and responsibilities can help mitigate the risks of insider threats and unauthorized access.
- Regular Security Audits and Vulnerability Assessments: Conducting regular security audits and vulnerability assessments can help identify and remediate security weaknesses in SCADA systems. Performing penetration testing, code reviews, and security scans can help identify vulnerabilities and ensure compliance with industry standards and regulatory requirements.
- Patch Management and Software Updates: Keeping SCADA systems up-to-date with the latest security patches and software updates is essential for mitigating the risks of cyberattacks and vulnerabilities. Implementing a robust patch management process can help ensure timely deployment of security updates and minimize the exposure to known vulnerabilities.
- Employee Training and Awareness: Providing comprehensive training and awareness programs for employees, contractors, and third-party vendors can help mitigate the risks of insider threats and human errors. Educating personnel about security best practices, social engineering techniques, and incident response procedures can help enhance the overall security posture of SCADA systems.
- Incident Response and Disaster Recovery Planning: Developing comprehensive incident response and disaster recovery plans can help organizations effectively respond to security incidents and minimize the impact on industrial operations. Establishing clear escalation procedures, incident reporting mechanisms, and backup and recovery strategies can help ensure business continuity and resilience in the face of cyber threats.
Conclusion
In conclusion, the security of SCADA systems is paramount for safeguarding critical infrastructure and ensuring the integrity, availability, and confidentiality of industrial operations. By implementing robust security measures, adhering to best practices, and fostering a culture of security awareness, organizations can mitigate the risks posed by cyber threats and protect the reliability and safety of SCADA systems. Ultimately, prioritizing SCADA security is essential for maintaining the resilience and sustainability of modern industrial operations in an increasingly interconnected world.